external-secrets
| Distro | external-secrets |
|---|---|
| Type | kubernetes-operator |
| Deploy | helm-chart |
| Docs | link |
| Backup | |
| Scaling | |
| CLI | |
| UI |
Architecture
Shared ClusterSecretStore:
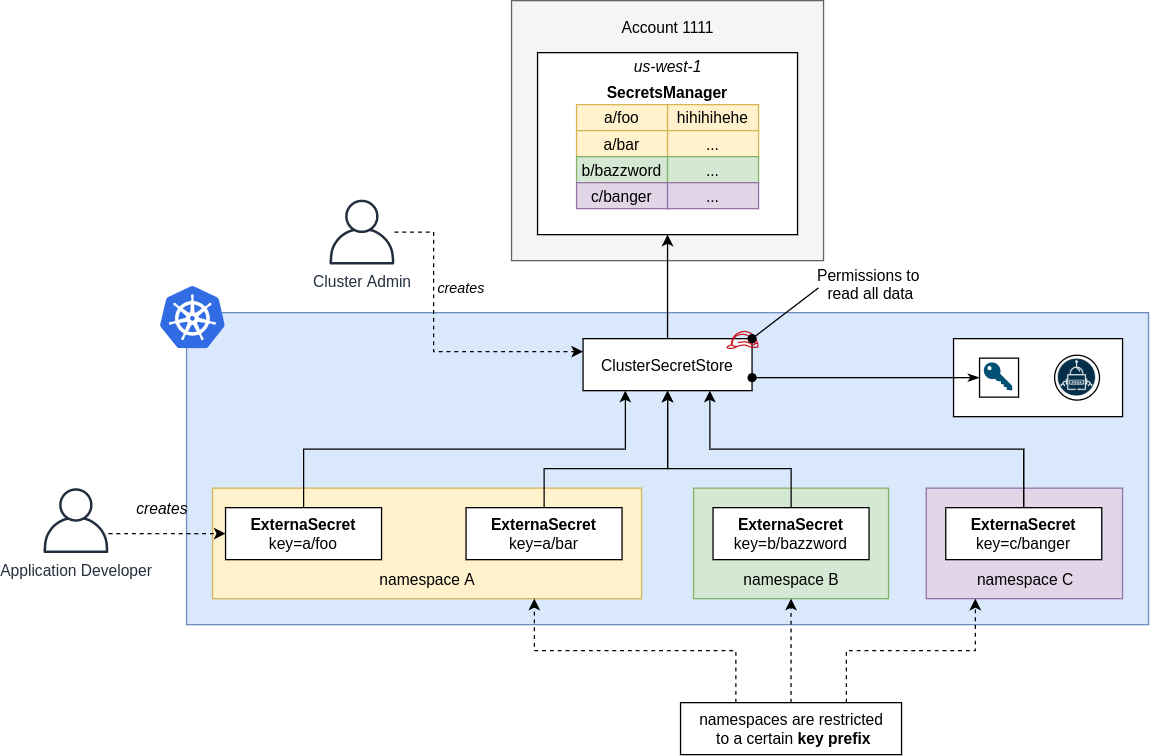
✅ Setup
✅ Hashicorp Vault
See Vault docs for more details.
-
Create a Vault engine path:
Secret Engines->Enable new engine +->KV-> Path:common -
Createa
ClusterSecretStorefor Vault
apiVersion: external-secrets.io/v1beta1
kind: ClusterSecretStore
metadata:
name: vault
spec:
provider:
vault:
server: "http://vault.vault.svc.cluster.local:8200"
path: "common"
version: "v2"
auth:
tokenSecretRef:
name: "vault-token"
namespace: vault
key: "token"
Usecases
✅ Basic: get secret, add secret from secret store
- example
ExternalSecretto read secret from secret store
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: test
namespace: default
spec:
refreshInterval: 10m
secretStoreRef:
name: vault
kind: ClusterSecretStore
target:
name: test
creationPolicy: Owner
dataFrom:
- extract:
key: "/test"
- example
PushSecretfrom k8s to secret store
Usecase: some resource created in k8s store its secret in k8s-secret, and we use PushSecret to save it in Vault and be accessible outside of k8s
cat <<EOF | kubectl apply -f -
---
apiVersion: external-secrets.io/v1alpha1
kind: PushSecret
metadata:
name: argocd-secret # Customisable
namespace: argocd # Same of the SecretStores
spec:
updatePolicy: Replace # Policy to overwrite existing secrets in the provider on sync
deletionPolicy: Delete # the provider' secret will be deleted if the PushSecret is deleted
refreshInterval: 10m # Refresh interval for which push secret will reconcile
secretStoreRefs: # A list of secret stores to push secrets to
- name: vault
kind: ClusterSecretStore
selector:
secret:
name: argocd-secret # Source Kubernetes secret to be pushed
data:
- conversionStrategy: None # Also supports the ReverseUnicode strategy
match:
# secretKey: best-pokemon # Source Kubernetes secret key to be pushed (comment out to push all keys)
remoteRef:
remoteKey: argocd/admin # Remote reference (where the secret is going to be pushed)
EOF
Common: generate secrets, update secrets, rotate secrets
✅ Monitoring
Grafana Dashboard
external-secrets:
serviceMonitor:
enabled: true
Maintenence
- Backup / Restore
- Scaling
- Upgrade