cert-manager
| Self-hosted | SaaS | |
|---|---|---|
| Name | cert-manager | |
| Type | kubernetes-operator | |
| Deploy | helm-chart | |
| Backup | manual | |
| Scaling | ||
| CLI | cmctl | |
| UI |
✅ Architectire
- creates TLS certificates for workloads in your Kubernetes or OpenShift cluster and renews the certificates before they expire.
- can obtain certificates from a variety of certificate authorities, including: Let's Encrypt, HashiCorp Vault, Venafi and private PKI.
- private key and certificate are stored in a Kubernetes Secret which is mounted by an application Pod or used by an Ingress controller
- With csi-driver, csi-driver-spiffe, or istio-csr , the private key is generated on-demand, before the application starts up; the private key never leaves the node and it is not stored in a Kubernetes Secret.
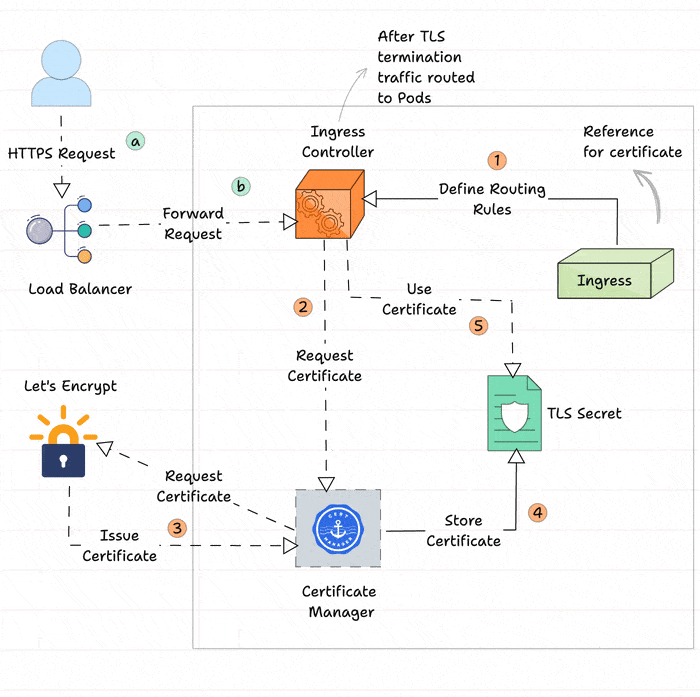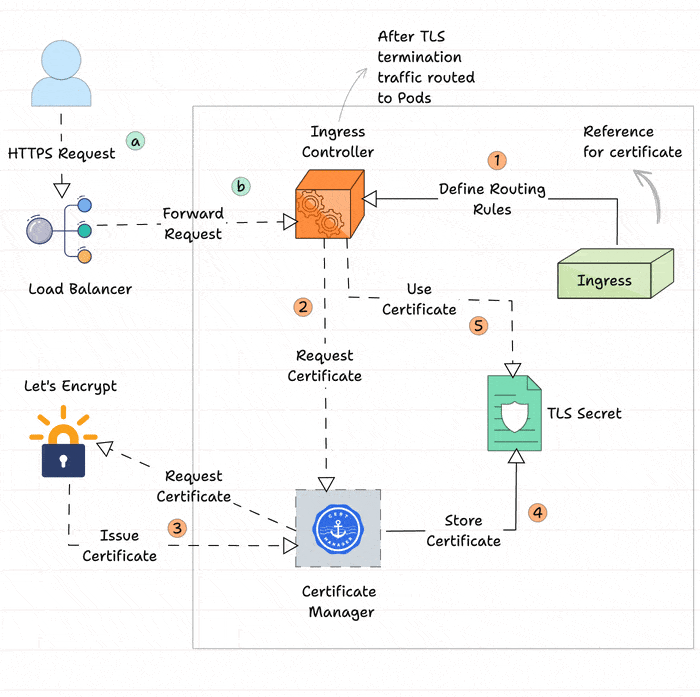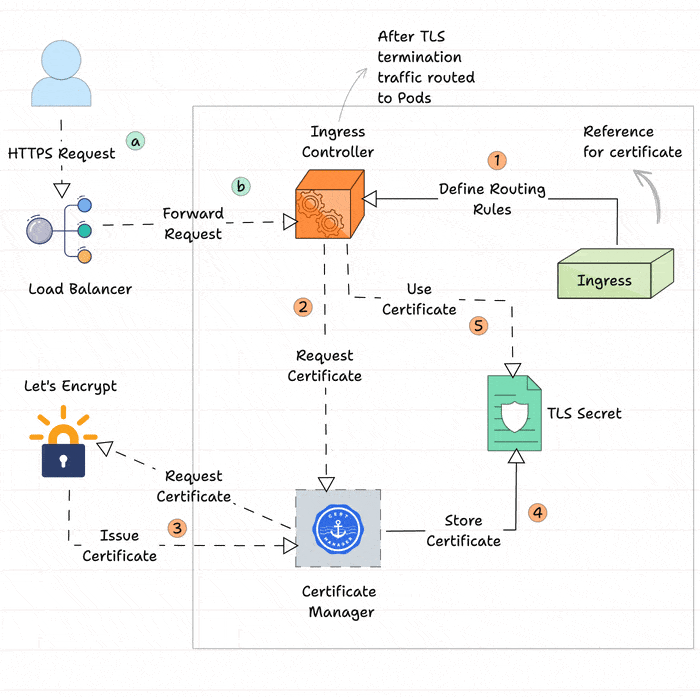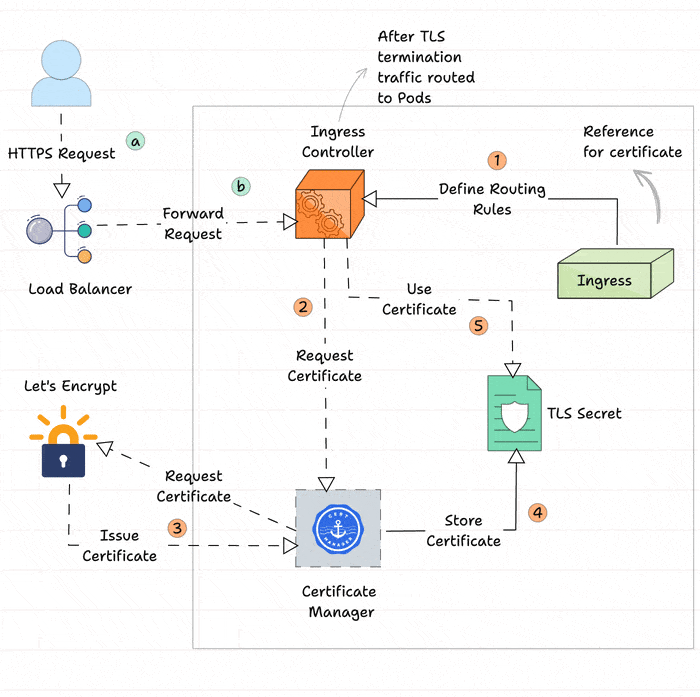
- The Ingress object will be created with the reference of the Cert Manager Issuers.
- The Ingress Controller will get the information from the Ingress object and request a certificate from the Cert Manager.
- The Cert Manager will request the Certificate Authority, for example, Let's Encrypt.
- After the verification, the CA will generate and provide the certificate to the Cert Manager.
- The generated certificate will be stored in Kubernetes as a TLS Secret.
- The Ingress Controller will encrypt the traffic using the stored certificate for the TLS termination.
- When a user tries to access the application, the external traffic is routed from the external Load Balancer to the Ingress Controller.
- The TLS termination will happen in the Ingress Controller with the TLS certificate and securely route the traffic to the application Pods.
Usecases
✅ Basic: TLS for local ingress-nginx (self-signed CA)
self-signe CA cert for local use
openssl genrsa -out ca.key 4096
openssl req -new -x509 -sha256 -days 365 -key ca.key -out ca.crt
sudo security add-trusted-cert -d -r trustRoot -k /Library/Keychains/System.keychain ca.crt
kubectl create secret generic -n vault ca --from-file=tls.crt=ca.crt --from-file=tls.key=ca.key
create a ClusterIssuer for self-signed CA
apiVersion: cert-manager.io/v1
kind: ClusterIssuer
metadata:
name: cluster-issuer-nginx
spec:
ca:
secretName: ca
create a Certificate for ingress-nginx
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: demo-cert
spec:
secretName: demo-tls-secret
issuerRef:
name: cluster-issuer-nginx
kind: ClusterIssuer
dnsNames:
- demo.home.lab
use secret created by Certificate in Ingress resource definition:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: demo
spec:
# . . .
tls:
- hosts:
- demo.home.lab
secretName: demo-tls-secret
Common: TLS for exposed ingress-nginx (Let's Encrypt)
Let's Encrypt Example
- letsencrypt
- cloudflare
- aws/gcp/azure
- vault-pki
Advanced: secure Istio service mesh
✅ Monitoring
Grafana Dashboard
- enable metrics and
PodMonitor
cert-manager:
prometheus:
enabled: true
podmonitor:
enabled: true
Maintenence
-
Install / Deploy
-
Backup / Restore
-
Scaling
-
Upgrade
Patform integration
how this tool integrated into a platform how to use it in a platform how to debug